Add Temporary IPv6 Address
su -
# include temporary IPv6 on lo
ip -6 addr add fc01::1/32 dev lo
Head to the terminal and access the server you intend to be COMP-0. As COMP-0 will later provide Re6st and IPv6 to the SlapOS network, there likely is no IPv6 available at this point. You need to add a temporary IPv6 address range as shown in the code above.
Rationale: SlapOS requires IPv6 internally and uses Re6st, which will be installed later to enable IPv6 in heterogeneous environments (distributed machines, different types).
You will later deploy and instantiate a Re6st registry on COMP-0 to provide IPv6 and Re6st access tokens. However, in order to deploy it, SlapOS needs to be installed and to install SlapOS, IPv6 is required. Thus, we use a temporary IPv6 address range until the Registry is available, at which point it will be removed again before correctly installing Re6st with IPv6 automatically being added.
Single Line Installer
sudo su
# wget deploy.erp5.net/slapos && bash slapos
...
What is the url to the SlapOS Master API? [https://slap.vifib.com/]:
What is the url to the SlapOS Master Website? [https://slapos.vifib.com/]:
What is this computer name? [noname]:
If you have slapos token if you have? [notoken]:
Continue and use the single line installer. You will be asked several questions during the installation. You are connecting to your own master, so on the first question, please point to port 5443 of your master's IPv4 adress (https://[IPv4]:5443) and on the second question, please add your SlapOS Master dashboard url https://[IPv4]:443/erp5/web_site_module/hostingjs/
Choose a name for your computer to identify it in your network and finally enter the association token you have received earlier. The installation can be repeated in case something goes wrong or you would like to change some of the entered parameters.
Once the installation has finishes without errors, you should see:
...
PLAY RECAP *********************************************************************
127.0.0.1 : ok=12 changed=4 unreachable=0 failed=0
In case installation fails and you want to start over, you need to request a new token as mentioned above and, depending on whether already created, remove any existing configuration in /etc/opt/slapos/slapos.cfg in COMP-0 before restarting.
You can verify that SlapOS was installed by trying:
# slapos node
watchdog RUNNING pid 13270, uptime 0:00:03
And (re)formatting the SlapOS node:
# slapos node format --now
2020-09-22 17:36:01 slapos[20980] INFO Updating computer
2020-09-22 17:36:07 slapos[20980] INFO Posting information to 'https://51.159.66.10:5443'
2020-09-22 17:36:08 slapos[20980] INFO slapos successfully prepared the computer.
Frontend Service Configuration
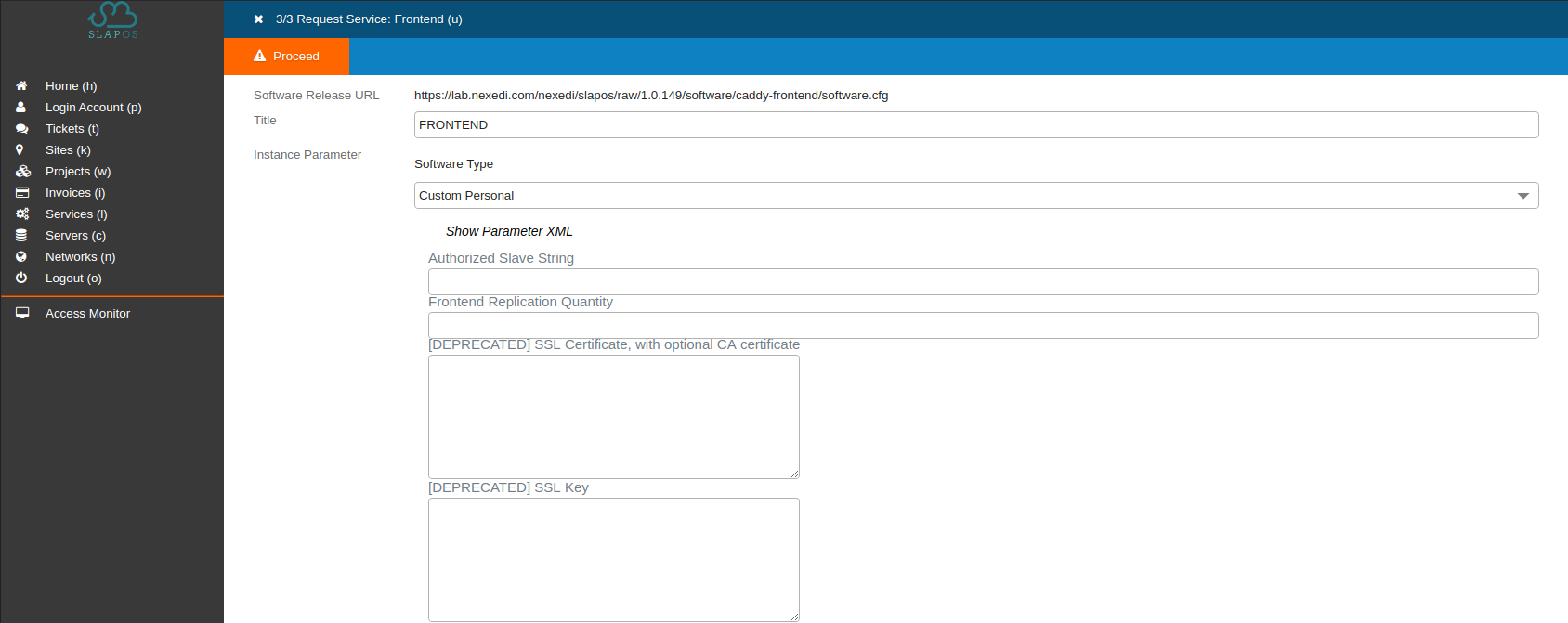
You will reach the Frontend configuration menu. It contains a form of software-specific parameters as well as a generic XML configuration field (hidden by default - click the "Show Parameter XML" button to display).
Select Software-Type custom personal, then fill the form. Don't forget to give the Frontend a title and make sure you select the computer you created at the end of the form. Otherwise the SlapOS Master will look by itself on which node the instance should be created (not relevant in this case as there is only one computer).
Fill the form like this :
- Title: FRONTEND
- Software type: Custom Personal
- Public IPv4: [IP_OF_YOUR_SERVER]
- Test Verification URL:
https://www.erp5.com/getId
- [DEPRECATED] SSL Certificate, with optional CA certificate: [AAA]
- [DEPRECATED] SSL Key: [BBB]
- Domain: [domain]
- Computer: [COMP-XXXX]
Alternatively, you can choose to click on the "Show parameter XML" button and fill the following XML configuration parameters:
<?xml version="1.0" encoding="utf-8"?>
<instance>
<parameter id="public-ipv4">[IP_OF_YOUR_SERVER]</parameter>
<parameter id="re6st-verification-url">https://www.erp5.com/getId</parameter>
<parameter id="apache-key">[AAA]</parameter>
<parameter id="apache-certificate">[BBB]</parameter>
<parameter id="domain">[domain]</parameter>
</instance>
using:
[IP_OF_YOUR_SERVER]: IPv4 address of your slave server (debian@xxx.this.one.xxx)- [AAA]: SSL Key (privkey.pem)
- [BBB]: SSL CA certificate (fullchain.pem)
[domain]: the domain you are using (here: slaptest.erp5.net)[COMP-XXXX]: computer where the partition for this Frontend will be created.
Click Proceed to start instantiation.
Instantiation and Port Forwarding
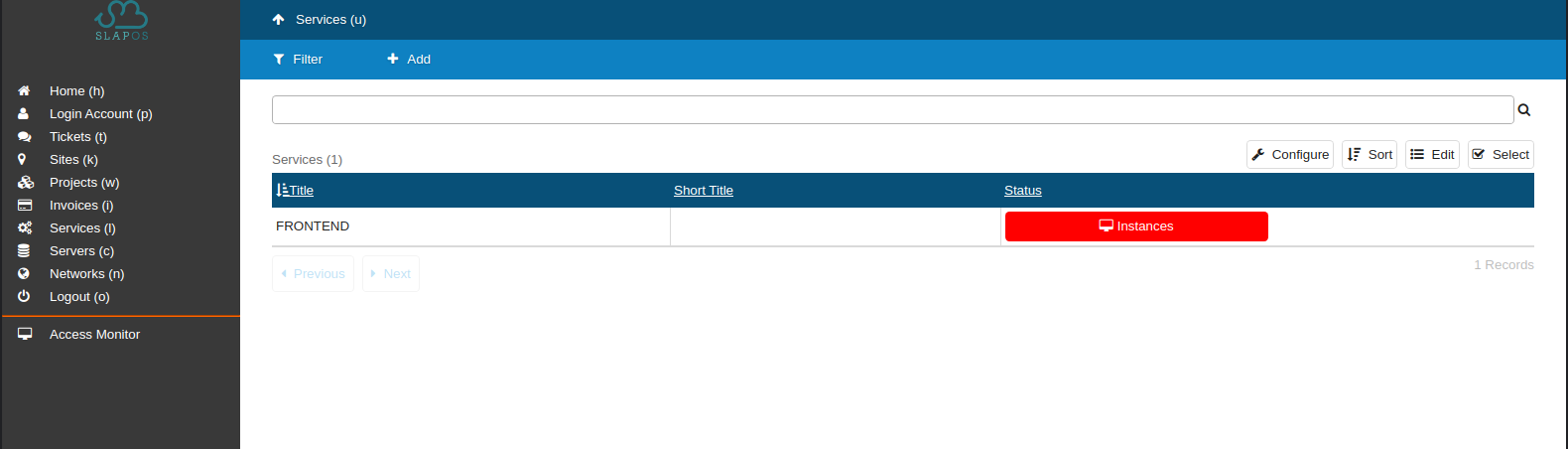
Refresh the list of current services to show the new service and status.
You can follow the compilation progress by looking at the slapos-node-instance.log using:
# tail /opt/slapos/log/slapos-node-instance.log -f
or calling # slapos node instance in the terminal directly.
The Frontend will be installed inside a computer partition and will listen on ports 8080 and 4443. Since permissions in Linux systems prevent users from accessing ports smaller than 1024, incoming traffic on public ports 80 and 443 has to be forwarded to the correct ports the Frontend is listening on.
So wait for the instantiation of the frontend, watch the log (as mentioned above). At the end, you should only see errors like: ERROR connection not possible while accessing 'https://softinst1.host.daetalus.cn/'. Those errors will disappear when you install socat and configure with it.
On your frontend server, use a Firewall with NAT traversal or use Socat. We will use Socat, a relay for bidirectional data transfer between two independent data channels. Data channels can be files, pipes, devices (terminal or modem, etc.), or sockets (Unix, IP4, IP6 - raw, UDP, TCP), etc. For more information, please refer to the Free Software Directory).
To install socat, head to your terminal and:
su -
# apt-get install socat
Find the local IPv4 addresses used by the Frontend in its configuration folder:
root@comp-0:~# grep '^:\|bind' /srv/slapgrid/slappart*/etc/Caddyfile
:4443 {
bind 10.0.97.156
:8080 {
bind 10.0.97.156
bind 10.0.97.156
ERROR while connecting to ('10.0.5.157', 26012): [Errno 111] Connection refused
Then call socat:
root@comp-0:~# socat TCP4-LISTEN:80,fork TCP4:10.0.97.156:8080 &
socat TCP4-LISTEN:443,fork TCP4:10.0.97.156:4443 &
To see whether your bindings are active, you can
root@comp-0:~# ps aux | grep socat
root 17629 0.0 0.0 6824 1960 pts/1 S 14:46 0:00 socat TCP4-LISTEN:80,fork TCP4:10.0.97.156:8080
root 17664 0.0 0.0 6824 3188 pts/1 S 14:46 0:00 socat TCP4-LISTEN:443,fork TCP4:10.0.97.156:4443
root 22300 0.0 0.0 6208 892 pts/1 S+ 15:08 0:00 grep socat
You can also verify that the port forwarding is working by accessing your Frontend url (in our case) foobar.slaptest.erp5.net in a browser. If successful, the listener should forward to the IPv4 address the Frontend is listening on and you should see the following:
This instance has not been found.
If this error persists, please check your instance URL and status on SlapOS Master.
In case the Frontend is not or no longer accessible, you can check on your node by:
sudo su
# slapos node
slappart7:6tunnel-26011-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27308, uptime 2:17:11
slappart7:6tunnel-26012-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27321, uptime 2:17:11
slappart7:6tunnel-4443-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27296, uptime 2:17:12
slappart7:6tunnel-8080-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27303, uptime 2:17:12
slappart7:bootstrap-monitor EXITED Sep 23 03:08 PM
slappart7:certificate_authority-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27314, uptime 2:17:11
slappart7:crond-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27329, uptime 2:17:11
slappart7:expose-csr_id-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27332, uptime 2:17:11
slappart7:frontend-caddy-safe-graceful EXITED Sep 23 03:08 PM
slappart7:frontend_caddy-db7c769e88f575f3926f31d8948f5fb9-on-watch RUNNING pid 27299, uptime 2:17:12
slappart7:kedifa-login-certificate-caucase-updater-on-watch RUNNING pid 28552, uptime 2:11:12
slappart7:kedifa-updater-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 28556, uptime 2:11:12
slappart7:monitor-httpd-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27337, uptime 2:17:11
slappart7:monitor-httpd-graceful EXITED Sep 23 03:08 PM
slappart7:trafficserver-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27305, uptime 2:17:11
slappart7:trafficserver-reload EXITED Sep 23 03:08 PM
slappart8:bootstrap-monitor EXITED Sep 23 02:46 PM
slappart8:caucase-updater-on-watch RUNNING pid 28026, uptime 2:13:44
slappart8:caucased-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26938, uptime 2:18:46
slappart8:certificate_authority-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26924, uptime 2:18:47
slappart8:crond-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26925, uptime 2:18:47
slappart8:expose-csr_id-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26923, uptime 2:18:47
slappart8:kedifa-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 28024, uptime 2:13:44
slappart8:kedifa-reloader EXITED Sep 23 02:46 PM
slappart8:monitor-httpd-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26939, uptime 2:18:46
slappart8:monitor-httpd-graceful EXITED Sep 23 02:46 PM
slappart9:bootstrap-monitor EXITED Sep 23 02:46 PM
slappart9:certificate_authority-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27075, uptime 2:18:00
slappart9:crond-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27076, uptime 2:18:00
slappart9:monitor-httpd-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27080, uptime 2:18:00
slappart9:monitor-httpd-graceful EXITED Sep 23 02:46 PM
slappart9:rejected-slave-publish-3df716aba73e4f0d660c97cd4a62564e-on-watch RUNNING pid 27079, uptime 2:18:00
watchdog RUNNING pid 19821, uptime 22:03:17
If the Frontend is running check if socat is working:
# ps aux | grep "socat"
root 17629 0.0 0.0 6824 1960 pts/1 S 14:46 0:00 socat TCP4-LISTEN:80,fork TCP4:10.0.97.156:8080
root 17664 0.0 0.0 6824 3188 pts/1 S 14:46 0:00 socat TCP4-LISTEN:443,fork TCP4:10.0.97.156:4443
root 22300 0.0 0.0 6208 892 pts/1 S+ 15:08 0:00 grep socat
If socat is not running anymore, redo the socat binding to reach the Frontend again.
Frontend Slave Running
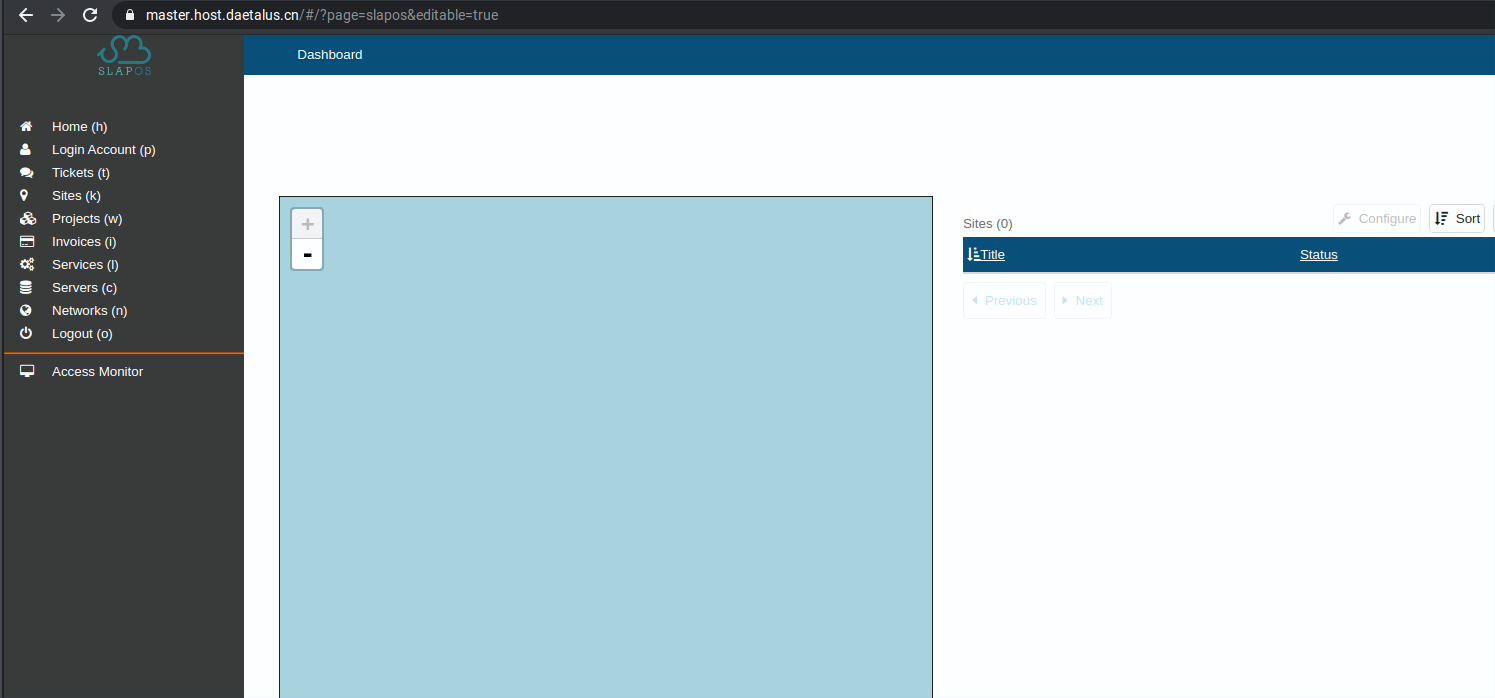
If you go to your requested URL (master.host.datetalus.cn in here) you can see that it points to the selected backend URL.
Should you have problems in loading the page, try restarting the Frontend by ssh-ing into your node, locating the frontend_apache-on-watch process and restarting it.
sudo su
# slapos node
slappart7:6tunnel-26011-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27308, uptime 3:42:54
slappart7:6tunnel-26012-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27321, uptime 3:42:54
slappart7:6tunnel-4443-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27296, uptime 3:42:55
slappart7:6tunnel-8080-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27303, uptime 3:42:55
slappart7:bootstrap-monitor EXITED Sep 23 04:32 PM
slappart7:certificate_authority-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27314, uptime 3:42:54
slappart7:crond-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27329, uptime 3:42:54
slappart7:expose-csr_id-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27332, uptime 3:42:54
slappart7:frontend-caddy-safe-graceful EXITED Sep 23 04:32 PM
slappart7:frontend_caddy-db7c769e88f575f3926f31d8948f5fb9-on-watch RUNNING pid 27299, uptime 3:42:55
slappart7:kedifa-login-certificate-caucase-updater-on-watch RUNNING pid 28552, uptime 3:36:55
slappart7:kedifa-updater-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 28556, uptime 3:36:55
slappart7:monitor-httpd-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27337, uptime 3:42:54
slappart7:monitor-httpd-graceful EXITED Sep 23 04:32 PM
slappart7:trafficserver-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27305, uptime 3:42:54
slappart7:trafficserver-reload EXITED Sep 23 04:32 PM
slappart8:bootstrap-monitor EXITED Sep 23 04:32 PM
slappart8:caucase-updater-on-watch RUNNING pid 28026, uptime 3:39:27
slappart8:caucased-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26938, uptime 3:44:29
slappart8:certificate_authority-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26924, uptime 3:44:30
slappart8:crond-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26925, uptime 3:44:30
slappart8:expose-csr_id-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26923, uptime 3:44:30
slappart8:kedifa-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 28024, uptime 3:39:27
slappart8:kedifa-reloader EXITED Sep 23 04:32 PM
slappart8:monitor-httpd-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 26939, uptime 3:44:29
slappart8:monitor-httpd-graceful EXITED Sep 23 04:32 PM
slappart9:bootstrap-monitor EXITED Sep 23 04:31 PM
slappart9:certificate_authority-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27075, uptime 3:43:43
slappart9:crond-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27076, uptime 3:43:43
slappart9:monitor-httpd-022ff02cd2a2f17a06435e15dcfcc561-on-watch RUNNING pid 27080, uptime 3:43:43you are waiting for,
slappart9:monitor-httpd-graceful EXITED Sep 23 04:31 PM
slappart9:rejected-slave-publish-3df716aba73e4f0d660c97cd4a62564e-on-watch RUNNING pid 27079, uptime 3:43:43
watchdog RUNNING pid 19821, uptime 23:29:00
To restart a service you can use slapos node restart slappart7:frontend_caddy-db7c769e88f575f3926f31d8948f5fb9-on-watch.
Socat Port Forwarding
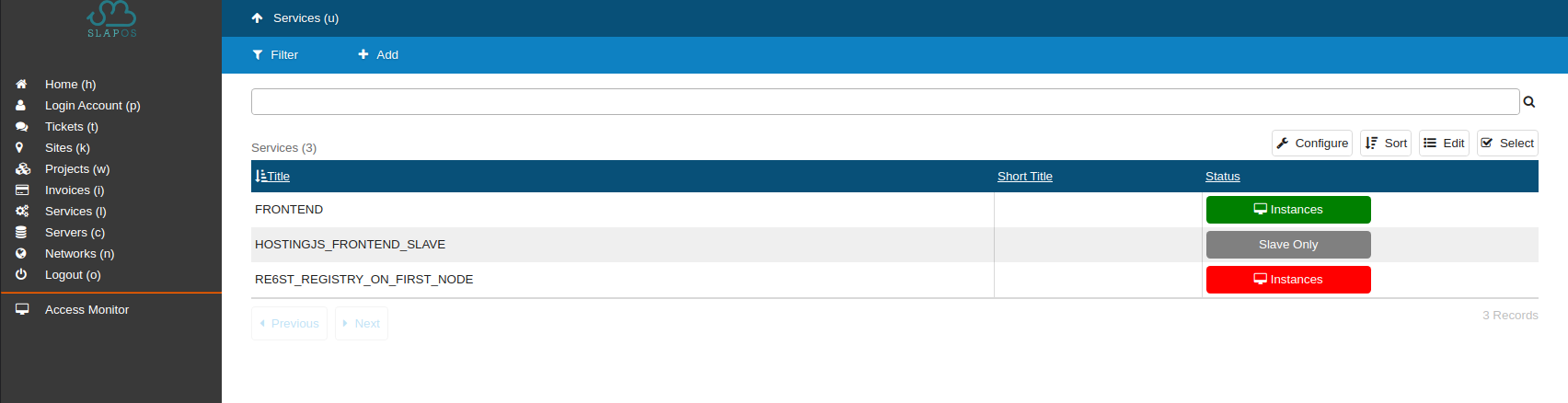
Refresh the page to show your instance and installation status.
You can follow the compilation by looking at the slapos-node-instance.log using:
# tail /opt/slapos/log/slapos-node-instance.log -f
or using slapos node instance directly.
As the Registry is listening on port 19201 and permissions in Linux systems prevent users from accessing ports below 1024, traffic must be forwarded.
This can be done using a Firewall with NAT traversal or using Socat. We will use Socat, a relay for bidirectional data transfer between two independent data channels. Data channels can be files, pipes, devices (terminal or modem, etc.), or sockets (Unix, IP4, IP6 - raw, UDP, TCP), etc. For more information, please refer to the Free Software Directory).
To install socat in case required, head to your terminal and:
sudo su # or su -
# apt install socat
Still in your terminal, start to see whether the Registry has finished installing (use # slapos node instance to follow installation):
root@comp-0:~# netstat -natp | grep 9201
tcp 0 0 10.0.175.168:9201 0.0.0.0:* LISTEN 11958/python2.7
tcp6 0 0 :::9201 :::* LISTEN 11958/python2.7
Find the IP using:
root@comp-0:~# ip -4 address show dev enp1s0
2: enp1s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
inet 51.159.66.11/24 brd 51.159.66.255 scope global enp1s0
valid_lft forever preferred_lft forever
Then call Socat with the listening tcp entry and the inet addr:
# socat TCP4-LISTEN:9201,fork,bind=51.159.66.11 TCP4:10.0.175.168:9201 &
Note, that your Registry master-url in the example is 51.159.66.11:9201. SAVE # THIS URL. You will need to provide it whenever you want to connect a new node to the network.
To verify whether port forwarding works, you can:
root@comp-0:~# ps aux | grep socat
root 17629 0.0 0.0 6824 3256 ? S Sep23 0:00 socat TCP4-LISTEN:80,fork TCP4:10.0.97.156:8080
root 17664 0.0 0.0 6824 3136 ? S Sep23 0:01 socat TCP4-LISTEN:443,fork TCP4:10.0.97.156:4443
root 27099 0.0 0.0 6824 452 ? S 17:08 0:00 socat TCP4-LISTEN:443,fork TCP4:10.0.97.156:4443
root 28530 0.0 0.0 6824 1900 pts/5 S 17:17 0:00 socat TCP4-LISTEN:9201,fork,bind=51.159.66.11 TCP4:10.0.175.168:9201
root 28539 0.0 0.0 6208 896 pts/5 S+ 17:17 0:00 grep socat
Before finishing make sure that any temporary IPv6 address space added during installation of the SlapOS node itself is removed. On your terminal, run:
sudo su
# ip -6 addr del fc01::1/32 dev lo
IPv6 will be reset when the first (gateway) node is being created.